The cost of cybercrime has risen by 10% in the past year alone. This number is especially alarming, considering that 43% of data breaches target small business victims.
If you manage or work with a tech team, it’s important to be aware of the different types of network security that are available so you can stay protected from these threats.
In this blog post, we’ll discuss the six main types of network security and how they can help keep your data safe.
Exploring The Importance of Network Security
Keeping your small business secure is no easy feat. And while internal IT teams may have been sufficient in the past, hackers are becoming more and more sophisticated each day, which makes it even harder to keep your data safe.
The many network security types all play a pivotal role in protecting your business from threats like malware, viruses and hacking attempts.
A managed service provider (MSP) can help by delivering a variety of services like:
- Anti-virus software
- Remote monitoring
- Firewalls
- Email security
- Different types of encryption in network security
- Network scanning
- Network segmentation
- Encryption and decryption
- Intrusion prevention systems (IPS)
- Access controls
All these features combined will give your business peace of mind that your operations are securely shielded from malicious attacks.
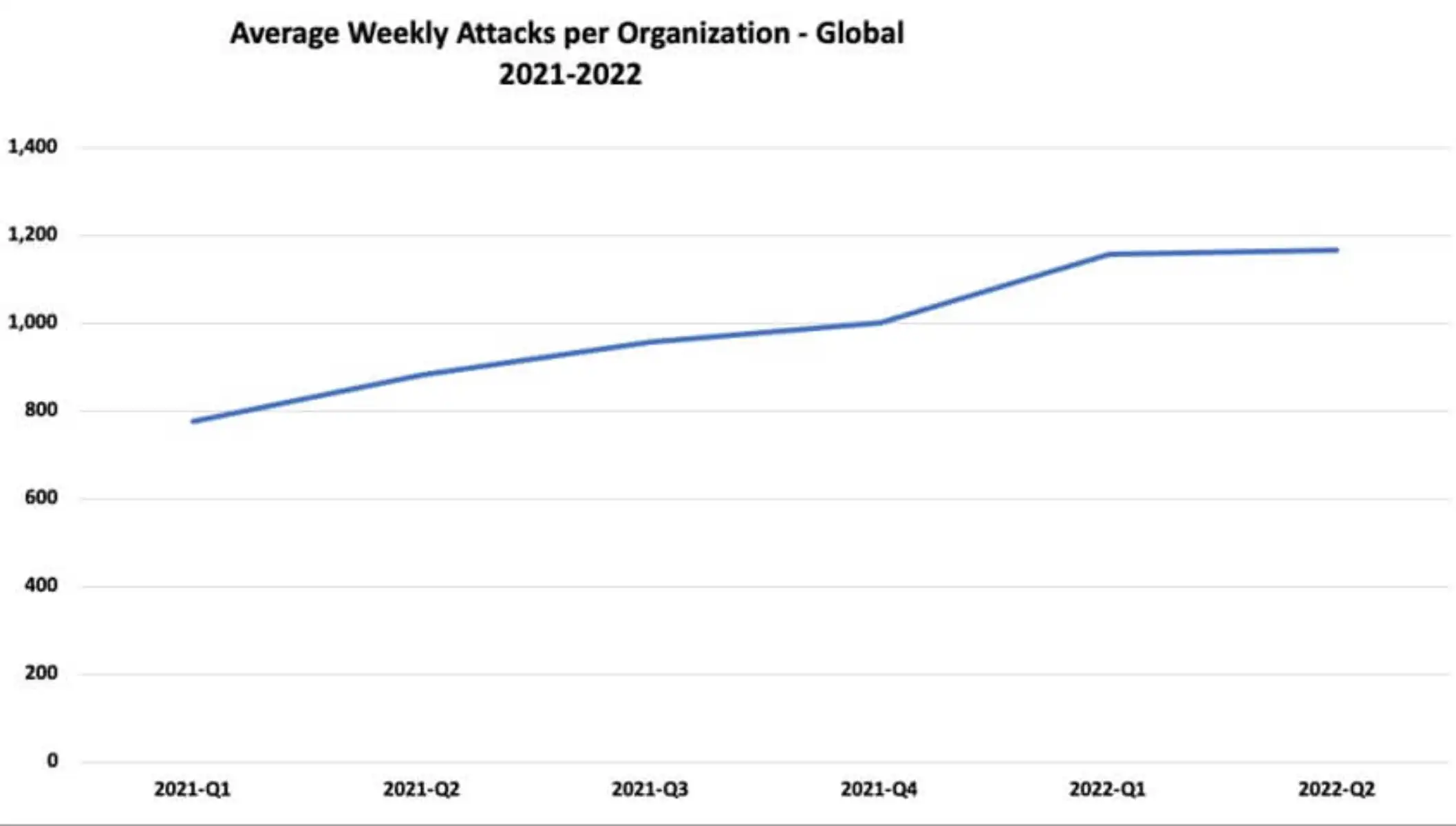
Image Credit: Check Point Research
With the global cost of data breach at $4.35 million in 2022 and the average number of attacks increasing by 38% between 2021 and 2022, the importance of network security in business has never been more evident.
Let’s explore some of the most common types of network security and how they can help.
6 Common Types of Network Security
1. Email Security
Email security is an important type of network security, consisting of measures to reduce the risk of criminals accessing or manipulating information exchanged via email.
Common components of email application security include advanced encryption standard (AES), spam protection, secure password standards, secure email hosting, and domain monitoring.
2. Intrusion Prevention System (IPS)
Intrusion prevention (IPS) is a security service that safeguards networks from malicious actors by detecting, analyzing and blocking suspicious activities.
Its components are composed of preventive measures such as firewall rules, antivirus software, and different types of scanning in network security. Meanwhile, it also provides corrective measures in the event of an attack, such as limiting traffic or sender/recipient blacklists.
Get Customized Network Security Built To ProtectFind Out How Advanced Networks Can Help |
3. Remote Monitoring
Remote monitoring helps your team identify trends and take proactive actions before the issues become too disruptive.
This technology utilizes monitoring agents that collect data on:
- Network performance
- Hardware/software health
- Real-time network activity
- IP addresses tracing
Remote system monitoring works by allowing you to define certain conditions through automation so that when any incongruities are detected, alerts can be sent to system administrators in real-time so proactive steps can be taken right away.
4. Access Controls
It is projected that the access control market alone will grow from $7.5 billion in 2018 to $12.1 billion by 2024, at an annualized rate of 8.24%.
As one of the most popular network security types, access controls provide security by restricting or allowing access to data, applications, files, networks, or other systems based on predetermined rules and criteria.
Common components of these controls include authentication/verification, authorization, roles-based privileges, segregation of duties, password policy enforcement, logging/auditing activity and redundant backups for additional security.
By implementing all these components in an effective manner, your organization gains a higher level of trust when it comes to protecting the integrity of digital assets.
5. Network Scanning
There are multiple types of scanning in network security that all play a crucial role in protecting your network. It’s important to regularly scan your network for vulnerabilities, so that malicious actors have fewer opportunities to enter your system and compromise your sensitive data.
The most common types of scanning are port scanning, vulnerability scanners, and service detection scans.
- Port scanning: helps to uncover open ports that could be entry points for malicious actors looking to gain access to an organization’s network.
- Vulnerability scanning: detect flaws in a system’s configuration that could lead to it being compromised if left unaddressed.
- Operating system or service detection scans: detect the type of operating systems or services installed on a device, which can help administrators assess whether those services are secure enough for use given your organization’s risk posture.
In short, network scanning is an invaluable tool for organizations looking to bolster their cyber security efforts. Check out these resources to learn more about the importance of cybersecurity:
|
Resources: |
6. Encryption
There are a number of different types of encryption in network security available, all with varying levels of protection to prevent unauthorized access.
What are the most common types?
- Symmetric key encryption: involves using a single, shared key; while asymmetric encryption uses two distinct but linked keys to keep messages safe.
- Public-key infrastructure (PKI) encryption: which incorporates authentication certificates, as well as data-in-transit protection such as SSL/TLS.
- Quantum encryption: which is used to protect large amounts of data across multiple locations and users.
- Private key encryption: uses a pair of keys, one public and one private, to encrypt and decrypt information. The public key is used to encrypt data that only the private key can decrypt.
By understanding what type of encryption is right for their specific circumstances, you can be sure that your sensitive information is kept safe and secure at all times.

Implementing the Different Types of Network Security
When it comes to implementing the different types of network security, a managed service provider (MSP) is an invaluable tool in ensuring your success.
By entrusting an experienced IT provider like Advanced Networks, we will help you identify vulnerabilities within your wireless networks and safeguard your digital assets accordingly.
Prioritize security with our expertise – book a free consultation to learn more about our wireless security offerings and how they can help.




