Employee Training and Awareness
Importance of Cybersecurity Education:
In today’s interconnected digital landscape, cybersecurity education is paramount. Employees are often the first line of defense against cyber threats. Understanding the fundamentals of cybersecurity empowers them to recognize potential risks, safeguard sensitive information, and contribute to the overall security of the organization. Cybersecurity education should cover various topics such as identifying social engineering tactics, recognizing malicious software, and understanding the importance of data privacy.
Recognizing and Avoiding Phishing Attempts:
Phishing attacks remain a prevalent threat, and employees must be equipped with the knowledge to identify and thwart these attempts. Training programs should educate employees on the common characteristics of phishing emails, such as suspicious links, unexpected attachments, or requests for sensitive information. Regular simulated phishing exercises can provide hands-on experience, helping employees develop a heightened sense of skepticism and critical thinking when interacting with emails or other communication channels.
Best Practices for Password Management:
Passwords are the frontline defense for securing access to sensitive systems and information. Training should emphasize the importance of creating strong, unique passwords and the risks associated with using easily guessable ones. Employees should be educated on the significance of multi-factor authentication (MFA) and its role in adding an extra layer of security. Regular updates on password policies and best practices, coupled with guidance on securely storing passwords, contribute to a robust defense against unauthorized access.
In summary, an effective Employee Training and Awareness program in cybersecurity serves as a proactive measure against evolving cyber threats. By instilling a culture of security consciousness, organizations can minimize the risk of breaches, protect sensitive data, and foster a resilient cybersecurity environment. Regular updates and refresher courses ensure that employees stay informed about the latest threats and maintain a vigilant stance in the face of ever-changing cybersecurity challenges.
Implementing Advanced Technologies
Implementing Advanced Technologies in cybersecurity is crucial for safeguarding digital assets and mitigating evolving threats. Three key components that play a pivotal role in fortifying cyber defenses are Artificial Intelligence (AI) and Machine Learning (ML), Next-Generation Firewalls (NGFWs), and Endpoint Security Solutions.
Artificial Intelligence and Machine Learning in Cybersecurity:
Artificial Intelligence and Machine Learning have revolutionized the field of cybersecurity by enabling proactive threat detection and response. AI algorithms can analyze vast amounts of data in real-time, identifying patterns and anomalies that might go unnoticed by traditional security measures. Machine Learning models continuously learn from new data, adapting to emerging threats and enhancing the overall efficacy of cybersecurity systems. AI-driven tools also automate routine tasks, allowing cybersecurity professionals to focus on strategic decision-making and threat intelligence analysis.
Next-Generation Firewalls:
Next-Generation Firewalls (NGFWs) represent a significant leap forward from traditional firewalls. These advanced security solutions combine traditional firewall capabilities with additional features such as intrusion prevention, application awareness, and deep packet inspection. NGFWs operate at the application layer, providing granular control over network traffic and preventing unauthorized access. With the ability to analyze and filter content, NGFWs enhance security by blocking malicious websites, malware, and other threats. Additionally, they offer advanced threat intelligence and can integrate with other security components to create a comprehensive defense strategy.
Endpoint Security Solutions:
Endpoint Security Solutions focus on protecting individual devices (endpoints) such as computers, mobile devices, and servers. With the increasing sophistication of cyber threats, securing endpoints has become paramount. These solutions encompass antivirus software, encryption tools, and advanced threat detection capabilities. Endpoint protection employs a multi-layered approach, combining signature-based detection, behavioral analysis, and heuristic analysis to identify and thwart diverse threats. As remote work becomes more prevalent, ensuring the security of endpoints is crucial for maintaining the integrity of organizational networks.
In conclusion, the implementation of AI and ML in cybersecurity enhances threat detection and response, NGFWs provide advanced network defense, and Endpoint Security Solutions secure individual devices in an interconnected digital landscape. Combining these advanced technologies creates a robust cybersecurity framework that is adaptive, proactive, and capable of defending against the ever-evolving threat landscape. Organizations that invest in these technologies not only bolster their security posture but also position themselves to stay ahead in the ongoing arms race against cyber adversaries.
Collaborative Approaches to Cybersecurity
Collaborative approaches to cybersecurity have become increasingly crucial in addressing the ever-evolving landscape of cyber threats. Organizations and governments worldwide recognize the need to work together to strengthen their collective defenses and ensure the resilience of critical infrastructures. Three key pillars of collaborative cybersecurity efforts include Public-Private Partnerships, Information Sharing and Threat Intelligence, and adherence to Industry Standards and Regulations.
Public-Private Partnerships (PPP):
Public-Private Partnerships play a pivotal role in fostering collaboration between government entities and private organizations. By leveraging the strengths of both sectors, PPPs can facilitate the exchange of information, resources, and expertise. Governments can provide regulatory frameworks, threat intelligence, and law enforcement capabilities, while private entities contribute innovative technologies, operational insights, and real-time data on emerging threats. This synergy enhances the overall cybersecurity posture and enables a more comprehensive response to cyber incidents.
Information Sharing and Threat Intelligence:
Timely and accurate information is a critical asset in the cybersecurity realm. Establishing mechanisms for information sharing and threat intelligence exchange allows organizations to stay ahead of cyber adversaries. Collaborative platforms enable the swift dissemination of threat indicators, attack patterns, and vulnerabilities among participating entities. This collective knowledge empowers organizations to proactively implement security measures, update defenses, and respond effectively to emerging threats. Initiatives such as the sharing of cybersecurity incident reports and best practices contribute to a more resilient and interconnected cybersecurity ecosystem.
Industry Standards and Regulations:
Adherence to industry standards and regulations is fundamental for establishing a baseline of cybersecurity practices across different sectors. Collaborative efforts in developing and implementing these standards ensure a unified and robust defense against cyber threats. Governments and industry stakeholders work together to define and enforce regulations that promote cybersecurity best practices, data protection, and incident response protocols. Compliance with these standards not only strengthens individual organizations but also fosters a culture of shared responsibility, creating a more secure digital environment for all stakeholders.
In conclusion, collaborative approaches to cybersecurity, including Public-Private Partnerships, Information Sharing and Threat Intelligence, and Industry Standards and Regulations, are essential for combating the dynamic and sophisticated nature of cyber threats. By leveraging the collective strength of governments, private sector entities, and regulatory frameworks, the global community can create a more resilient and secure cyberspace for the benefit of individuals, businesses, and nations alike.
Incident Response and Recovery
Incident Response and Recovery (IRR) is a crucial component of an organization’s cybersecurity framework, encompassing a systematic approach to handling and mitigating security incidents. This involves the development of a robust Incident Response Plan (IRP), regular testing of incident response procedures, and a continuous learning process from past incidents to enhance future responses.
Developing an Incident Response Plan (IRP):
Creating a comprehensive Incident Response Plan is foundational to effective incident management. The IRP should outline a well-structured and documented set of procedures to follow when a security incident occurs. This involves defining the roles and responsibilities of the incident response team, establishing communication channels, and determining the escalation process. The plan should also include incident identification, containment, eradication, recovery, and lessons learned phases. Regularly updating and refining the IRP in response to changes in the threat landscape, technology, or organizational structure is essential to ensure its effectiveness.
Regularly Testing Incident Response Procedures:
Testing incident response procedures through simulation exercises is vital for assessing the preparedness of the organization to handle real-world security incidents. These exercises can take the form of tabletop simulations, red teaming, or even full-scale drills. Testing helps identify gaps or weaknesses in the incident response process, enabling organizations to refine their procedures and train their response teams effectively. Regular testing not only validates the efficacy of the IRP but also ensures that personnel are familiar with their roles and can respond promptly and effectively in a high-pressure situation.
Learning from Past Incidents to Improve Future Responses:
Post-incident analysis plays a critical role in enhancing an organization’s resilience to cyber threats. After an incident is successfully mitigated, a thorough review should be conducted to identify the root causes, tactics, techniques, and procedures employed by the threat actor. This analysis should extend beyond technical aspects to include an examination of procedural and human factors. Documenting these findings and incorporating them into the organization’s knowledge base allows for continuous improvement. This iterative process helps organizations adapt their IRPs, update security controls, and provide additional training to personnel based on the lessons learned from each incident.
In summary, Incident Response and Recovery is a dynamic and evolving aspect of cybersecurity, requiring proactive measures such as the development of a comprehensive IRP, regular testing of procedures, and a continuous learning culture that draws insights from past incidents. By adhering to these principles, organizations can strengthen their ability to detect, respond to, and recover from security incidents effectively.
Regulatory Compliance
Regulatory Compliance in the realm of data protection is a critical facet that organizations must meticulously navigate to uphold the integrity of their operations. This entails a comprehensive understanding of various data protection regulations worldwide.
Overview of Data Protection Regulations:
In today’s interconnected digital landscape, data protection regulations have become increasingly stringent to safeguard individuals’ privacy and maintain the trust of stakeholders. A pivotal aspect is the General Data Protection Regulation (GDPR) in the European Union, which sets a high standard for data protection globally. It mandates organizations to acquire explicit consent for data processing, disclose data usage purposes, and implement robust security measures.
Additionally, other jurisdictions, such as the California Consumer Privacy Act (CCPA) in the United States and the Personal Information Protection and Electronic Documents Act (PIPEDA) in Canada, have introduced similar frameworks. These regulations emphasize transparency, accountability, and the rights of individuals concerning their personal information.
Ensuring Compliance with Global Standards:
To navigate the complex landscape of data protection regulations, organizations need to adopt a proactive approach. This involves establishing a robust compliance framework that aligns with global standards. Implementing privacy by design principles, conducting regular privacy impact assessments, and appointing a Data Protection Officer are essential steps in this direction.
Moreover, organizations operating across borders must be cognizant of the variances in regulations. Tailoring compliance strategies to adhere to specific jurisdictional requirements ensures a comprehensive and adaptable approach. Utilizing encryption technologies, access controls, and secure data storage practices further fortify an organization’s commitment to global data protection standards.
Transitioning seamlessly between these global standards demands ongoing vigilance, necessitating regular updates to policies and practices in response to evolving regulatory landscapes. This adaptability is crucial to fostering a culture of compliance within an organization.
Penalties for Non-Compliance:
Non-compliance with data protection regulations can have severe consequences, both financially and reputationally. Regulatory bodies have the authority to impose substantial fines for violations, with penalties often scaling proportionally to the severity of the breach. Beyond financial repercussions, organizations may face legal actions, damaged reputations, and a loss of customer trust.
Understanding the potential penalties for non-compliance underscores the importance of a proactive and vigilant approach to regulatory adherence. Organizations must invest in robust data protection measures not only to mitigate the risk of financial penalties but also to demonstrate a commitment to ethical data handling practices.
In conclusion, navigating the intricate landscape of regulatory compliance in data protection necessitates a comprehensive understanding of global standards, a proactive approach to compliance, and a keen awareness of the penalties for non-compliance. By embracing these principles, organizations can safeguard sensitive information, foster trust, and navigate the evolving regulatory terrain with confidence.
The Future of Cyber Security
The landscape of cybersecurity is continually evolving, shaped by emerging technologies and the ever-present threat of malicious actors. As we peer into the future of cybersecurity, several key elements stand out, underscoring the need for constant vigilance and innovation in the realm of digital defense.
Emerging Technologies and Threats:
In the dynamic realm of cybersecurity, staying ahead of emerging technologies is paramount. The proliferation of Internet of Things (IoT) devices, 5G networks, and quantum computing brings both promises and perils. The interconnectivity of IoT devices expands the attack surface, while the unprecedented processing power of quantum computing poses a potential threat to traditional encryption methods.
Furthermore, as technology advances, so do the techniques employed by cybercriminals. The rise of artificial intelligence (AI) in cyberattacks is a growing concern. AI-powered malware can adapt and evolve in real-time, making it increasingly difficult for conventional security measures to keep pace. As we embrace innovations like smart cities, autonomous vehicles, and decentralized networks, the attack vectors diversify, necessitating a proactive and adaptive approach to cybersecurity.
The Role of Artificial Intelligence in Enhancing Security:
Artificial intelligence is not merely a double-edged sword; it is also the shield in the ongoing battle for digital security. AI, when harnessed for defensive purposes, can fortify cybersecurity infrastructure by autonomously identifying and mitigating threats. Machine learning algorithms can analyze vast datasets, detecting patterns and anomalies that may elude human observation.
Moreover, AI can enhance incident response times, providing a swift and effective countermeasure against cyber threats. From predictive analysis to behavioral analytics, artificial intelligence serves as a force multiplier, enabling cybersecurity professionals to anticipate and thwart attacks before they manifest fully.
While AI contributes significantly to defensive strategies, ethical considerations and the risk of adversaries leveraging AI for malicious purposes must not be overlooked. Striking a delicate balance between innovation and security is imperative as the symbiotic relationship between AI and cybersecurity evolves.
Cybersecurity Trends and Predictions:
Looking ahead, several trends and predictions shape the trajectory of cybersecurity. Zero-trust architectures are gaining prominence, advocating for a fundamental shift from perimeter-based security to a model where trust is never assumed, regardless of the user’s location or network connection. This approach reflects the growing realization that traditional defense mechanisms are insufficient in the face of sophisticated cyber threats.
Cloud security continues to be a focal point, with organizations increasingly relying on cloud-based services. This shift prompts the need for robust cloud security measures, emphasizing data encryption, access controls, and continuous monitoring.
As the world becomes more interconnected, the significance of international collaboration in cybersecurity cannot be overstated. Cyber threats transcend borders, demanding a unified and coordinated response from the global community. Governments, businesses, and individuals must collaborate to share threat intelligence, best practices, and resources to fortify the collective defense against cyber adversaries.
The future of cybersecurity is a multifaceted tapestry, woven with the threads of emerging technologies, the symbiotic relationship with artificial intelligence, and the evolving landscape of trends and predictions. Adapting to these dynamics requires a holistic and collaborative approach, ensuring that our digital world remains secure and resilient in the face of ever-evolving cyber threats.
Securing Sensitive Data: Strengthening Cybersecurity Measures for Businesses in the Los Angeles and Orange County Regions.
In conclusion, the continuous evolution of cybersecurity stands as an imperative response to the ever-growing and sophisticated threats in the digital landscape. As technology advances, so do the methods employed by cybercriminals, necessitating a dynamic and proactive approach to safeguarding sensitive data.
The realization of collective responsibility for protecting sensitive data underscores the interconnected nature of our digital world. Organizations, individuals, and governments alike must recognize their role in contributing to a robust cybersecurity ecosystem. Collaborative efforts, information sharing, and the adoption of best practices are essential elements in building a resilient defense against cyber threats.
Looking forward, the path to a secure and resilient cyber landscape requires a multifaceted strategy. Investment in cutting-edge technologies, continuous training and education, and the establishment of international norms and regulations are vital components. Additionally, fostering a culture of cybersecurity awareness and responsibility at all levels will contribute to creating a more secure digital environment.
As we navigate the complex challenges of the digital age, it is crucial to remain vigilant, adaptable, and committed to the ongoing enhancement of cybersecurity measures. By embracing collective responsibility and forging a united front, we can mitigate risks, protect sensitive data, and pave the way for a future where the digital landscape is secure and resilient.




 Seamless Onboarding: Elevating Employee Success with Standardized Technology Protocols
Seamless Onboarding: Elevating Employee Success with Standardized Technology Protocols



 We are creative and artistic when it comes to working. We love to create and do what we are passionate about. Doing what we love brings us join and excitement, but that can all be taken away by the use of computers, typing and busy work. Microsoft Office 365 has notice the announce of doing busy work and did what is loves to do, create. Just released on Martin Luther King Jr. Day is
We are creative and artistic when it comes to working. We love to create and do what we are passionate about. Doing what we love brings us join and excitement, but that can all be taken away by the use of computers, typing and busy work. Microsoft Office 365 has notice the announce of doing busy work and did what is loves to do, create. Just released on Martin Luther King Jr. Day is


 Laptop WorkStations:
Laptop WorkStations: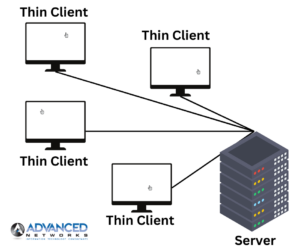 Thin client workstations offer a streamlined and cost-effective computing solution by offloading most of the processing tasks to a central server. These lightweight terminals rely on the server for computing power, storage, and software applications, reducing the need for extensive hardware at the user’s end. Thin client workstations are particularly beneficial in environments where centralized management, security, and resource optimization are top priorities. With minimal local processing, these workstations are easy to deploy, maintain, and secure. They are an excellent choice for organizations seeking efficient, scalable solutions that minimize hardware costs and simplify IT administration. Thin client workstations contribute to a more centralized and agile IT infrastructure, making them a preferred choice for businesses aiming to streamline operations and enhance overall efficiency.
Thin client workstations offer a streamlined and cost-effective computing solution by offloading most of the processing tasks to a central server. These lightweight terminals rely on the server for computing power, storage, and software applications, reducing the need for extensive hardware at the user’s end. Thin client workstations are particularly beneficial in environments where centralized management, security, and resource optimization are top priorities. With minimal local processing, these workstations are easy to deploy, maintain, and secure. They are an excellent choice for organizations seeking efficient, scalable solutions that minimize hardware costs and simplify IT administration. Thin client workstations contribute to a more centralized and agile IT infrastructure, making them a preferred choice for businesses aiming to streamline operations and enhance overall efficiency. Virtual Desktop Infrastructure (VDI) is a technology that enables the creation and management of virtualized desktop environments on a centralized server. In a VDI setup, individual desktop instances run as virtual machines on a server, and users access these desktops remotely using thin clients or other devices. VDI provides a flexible and scalable solution for delivering desktop experiences to end-users, allowing them to access their virtual desktops from anywhere with an internet connection.
Virtual Desktop Infrastructure (VDI) is a technology that enables the creation and management of virtualized desktop environments on a centralized server. In a VDI setup, individual desktop instances run as virtual machines on a server, and users access these desktops remotely using thin clients or other devices. VDI provides a flexible and scalable solution for delivering desktop experiences to end-users, allowing them to access their virtual desktops from anywhere with an internet connection. High-performance workstations are computing systems engineered to deliver exceptional speed, power, and efficiency, making them well-suited for tasks demanding substantial computational resources. Typically equipped with advanced processors, substantial RAM, and dedicated graphics cards, these workstations excel in handling resource-intensive applications such as 3D rendering, scientific simulations, video editing, and complex data analysis.
High-performance workstations are computing systems engineered to deliver exceptional speed, power, and efficiency, making them well-suited for tasks demanding substantial computational resources. Typically equipped with advanced processors, substantial RAM, and dedicated graphics cards, these workstations excel in handling resource-intensive applications such as 3D rendering, scientific simulations, video editing, and complex data analysis. Cloud workstations represent a modern paradigm in computing, offering a scalable and flexible solution that leverages cloud infrastructure to deliver virtualized desktop environments. With cloud workstations, the traditional model of having physical desktop hardware is replaced by virtual machines hosted in the cloud. Users can access their desktop environments remotely, from a variety of devices, enhancing mobility and facilitating remote work.
Cloud workstations represent a modern paradigm in computing, offering a scalable and flexible solution that leverages cloud infrastructure to deliver virtualized desktop environments. With cloud workstations, the traditional model of having physical desktop hardware is replaced by virtual machines hosted in the cloud. Users can access their desktop environments remotely, from a variety of devices, enhancing mobility and facilitating remote work.


