It’s no secret that more and more businesses are taking advantage of the incredible benefits of encryption for safeguarding sensitive information and data.
In fact, encryption is quickly becoming a necessity in order to protect data from being accessed or stolen by hackers. And what’s more, doing so is proven to save businesses big money for each attack (an average of $1.4 million)!
While encryption has always been critical for financial institutions and other organizations handling sensitive data, it is now becoming increasingly important for businesses in other industries as well.
In this blog we’re going to take you on a guided tour of all things encryption-based. We’ll teach you a little bit about the various types of data encryption that exist, then explain to you the biggest 5 encryption benefits the eponymous cyber security solution can afford you.
What is Data Encryption and What are the Various Types (and What Do They Do)?
Source:SSLStore
Data encryption is the process of scrambling data in order to make it unreadable and indecipherable by anyone who doesn’t have the right key or password.
Simply put, the data can only be viewed if someone has access to a secret code (key), which enables them to unscramble the encrypted information.
Now that you know what encryption is, let’s look at some of the different types of encryption used in today’s information security solutions:
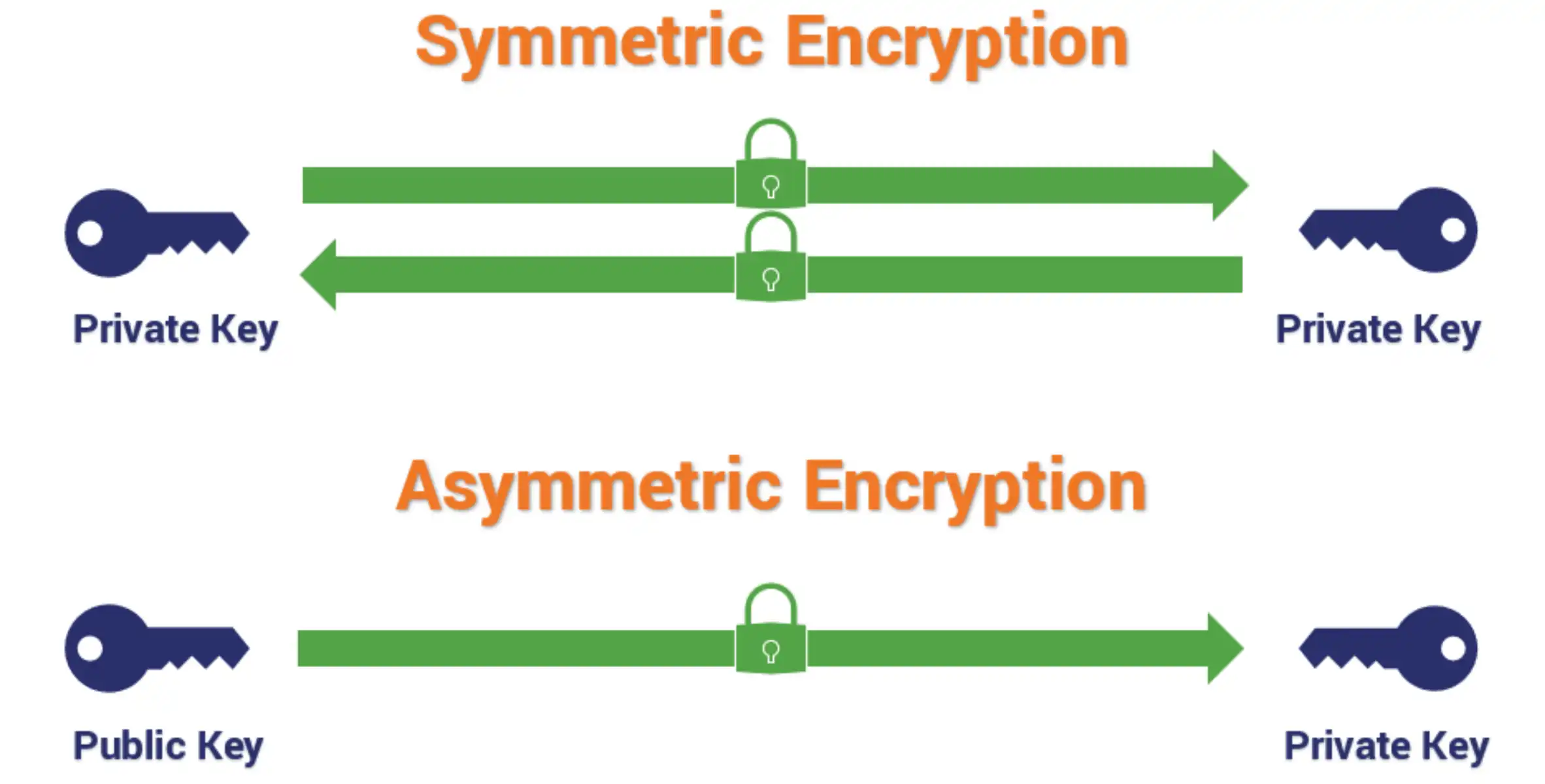
Symmetric Encryption
This type of encryption uses just one key for both encrypting and decrypting data. It is used more often than not because it’s faster and less taxing on resources than other methods.
Asymmetric Encryption
This type of encryption uses two different encryption keys for encrypting and decrypting data (one public key, one private key). It is more secure than symmetric encryption but slower in terms of processing speed.
Hashing
Hashing is used to create a unique identifier or “fingerprint” for a file; it cannot be reversed to get the original information. It is mainly used as an authentication tool.
The Top 5 Benefits of Data Encryption You Should Know About
Now that you know what encryption is and what types are available, let’s move onto the 5 benefits of encryption technology in your business:
1) Enhanced Security
The most obvious benefit of using encrypted data is enhanced security and data protection. Encrypted data can’t be accessed without the correct key, which means that hackers will have a much harder time breaking into your systems or networks.
2) Improved Data Integrity
Encryption algorithms help to protect data from unauthorized alteration, which is important for maintaining the accuracy and consistency of the data. This can be especially helpful for organizations dealing with large amounts of complex information.
Avoid Having Your Data Being Stolen or Lost Forever!Our backup and disaster recovery solutions make sure your data stays with you. |
3) Increased Privacy
Encryption also helps to ensure privacy by making it more difficult for third parties to access sensitive consumer data. This is essential for businesses that handle customer information or credit cards and need to comply with privacy regulations such as GDPR.
4) Cost Savings
Implementing encryption technology often costs less than defending against cyberattacks, meaning organizations can save money in the long run by investing in encryption solutions now.
5) Regulatory Compliance
Many regulatory bodies require organizations to use encryption technology in order to comply with data security standards. This is especially true for businesses that handle sensitive financial or health data, as well as those in certain industries like banking and healthcare.
Examining the Benefits of Encryption
While there are many advantages and disadvantages of data encryption, the benefits to businesses far outweigh the cons, including enhanced security, improved data integrity, increased privacy and cost savings.
Investing in the right type of encryption solutions can be invaluable for ensuring that sensitive data remains safe, secure, and compliant. It’s up to you to decide which type of solution best suits your needs, but rest assured that whatever you choose will have a positive impact on protecting your business from malicious actors.
As more businesses are recognizing the importance of encryption and its various benefits (including the benefits of encrypting your phones), investing in the right cyber security solution is becoming increasingly important.
In order to make sure that your business is properly protected from malicious actors and data breaches, it’s essential to find a reliable encryption solution that can meet your needs. Investing in the right type of solution can help safeguard against costly data breaches and help you remain compliant with industry regulations.
|
Learn these other essential cyber security insights to prevent being a cyber-victim: |
Capitalizing on the Advantages of Encryption with Advanced Networks
Encryption is becoming increasingly important in today’s digital world, as businesses need to be able to protect their sensitive data from malicious actors.
Whatever your reasons for encryption, Advanced Networks offers a variety of solutions that can help organizations ensure the security and integrity of their information. With our encryption technology, businesses can take advantage of features like end-to-end encryption, two-factor authentication, and more. This ensures that any data sent over a network is adequately secured and cannot be accessed by unauthorized parties.
Contact us today to learn more about how our encryption solutions can elevate your data security.